Social engineering plays a role in many cybersecurity attacks.
What is Social Engineering?
To begin with, attempts to gain access to your accounts or gather your personal information can come from anywhere: Facebook, Twitter, phone calls, text, etc. These are all vectors people may use to do this. All of this is called social engineering. This is defined as “the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.”
Every day, we deal with the issue of determining whether some form of communication we receive can be trusted or not. Unfortunately, it’s getting to the point where this thought process is almost automatic. So again, we want to highlight the things to look out for, so you don’t fall victim.
Social Engineering Is Sneaky! Be Careful If…
It Seems Urgent
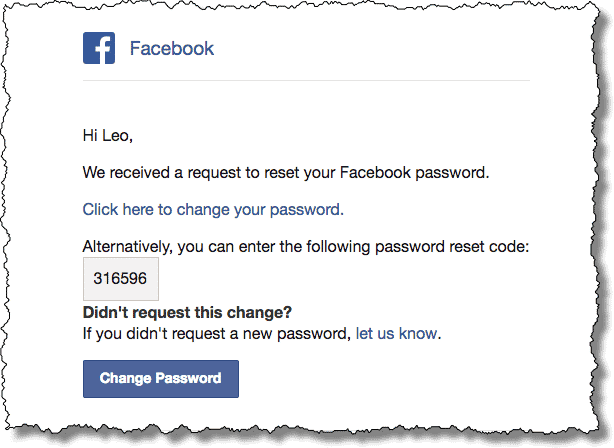
Many social engineering/phishing emails attempt to generate a sense of urgency (generally time sensitive). This tactic is designed to cause panic and hopefully keep you from making good decisions. Here is an example:
“If you don’t reset your password now all of your emails will be deleted!!”
Of course, an email host would never do this. Not all people realize this, and some might panic, follow the instructions in the email, and hand over their account credentials. I’m sure you’ve had friends on Facebook say, “Don’t open the link I sent you. My account has been hacked!” This is a common form of social engineering.
The general rule of thumb is, if you didn’t request the reset password link, IT’S A PHISHING SCAM. However, if you still want to reset your password, go directly to the site and do it there.
It Seems Official
It’s common for senders to also attempt to impersonate official agencies or use a well-known name to get what they want. Remember, the IRS is NOT going to email or call you asking for your social security number. They already have your information on file.
The most common ones we see come in two forms:
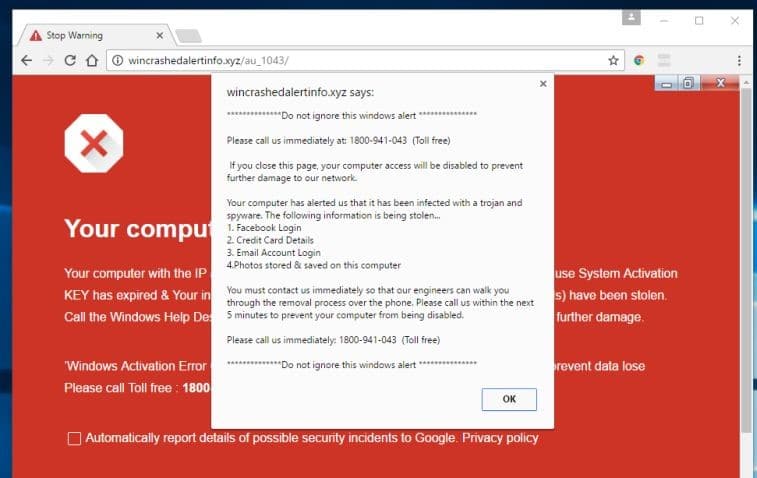
The first is the dreaded 1-800 pop-up that you may get on your computer saying, “you’re infected with a virus!” and to call a number right away. Calling the number will connect you with a “technician” that will attempt to log into your computer and then persuade you to pay a cleanup fee to resolve your issue. The warning message you get is a pop up being generated from an infected website (NOT a virus on your computer). Generally, closing your browser or just rebooting your computer resolves this.
The second is a “too good to be true” scenario. The target will receive a phone call from Microsoft or some other well-known entity. Then they will let you know that, due to them going out of business, they would like to refund you the remainder of the warranty or service that you purchased. Finally, they’ll ask you for your bank account or credit card so they can send you the refund.
It would be fantastic if someone called me to give me money. But unfortunately, it has never happened. If you ever get a call like this just hang up the phone. Do not engage the caller.
Hopefully with this information you will be better equipped to deal with potential scams that come your way.